What is a Cyber Attack?
Cyber attacks are unwelcome attempts to steal, expose, alter, disable or destroy information through unauthorized access to computer systems.
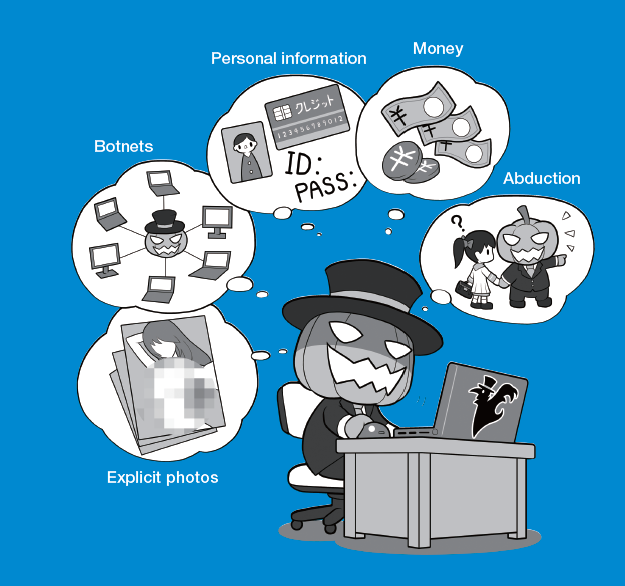
1. What is a Cyber Attack?
A cyber attack is an assault launched by cybercriminals using one or more computers against a single or multiple computers or networks.
A cyber attack can maliciously disable computers, steal data, or use a breached computer as a launch point for other attacks. Cybercriminals use a variety of methods to launch a cyber attack, including malware, phishing, ransomware, denial of service, among other methods.
2. Why cyber attacks happen?
In addition to cybercrime, cyber attacks can also be associated with cyber warfare or cyberterrorism, like hacktivists. Motivations can vary, in other words. And in these motivations, there are three main categories: criminal, political and personal.
Criminally motivated attackers seek financial gain through money theft, data theft or business disruption. Likewise, the personally motivated, such as disgruntled current or former employees, will take money, data or a mere chance to disrupt a company’s system.
However, they primarily seek retribution. Socio-political motivated attackers seek attention for their causes. As a result, they make their attacks known to the public—also known as hacktivism.
Other cyber attack motivations include espionage, spying—to gain an unfair advantage over competitors—and intellectual challenge.
3. Who is behind cyber attacks?
Criminal organizations, state actors and private persons can launch cyber attacks against enterprises. One way to classify cyber attack risks is by outsider versus insider threats.
4. What do cyber attackers target?

Cyberattacks happen because organizations, state actors or private persons want one or many things, like:
- Business financial data
- Clients lists
- Customer financial data
- Customer databases, including personally identifiable information (PII)
- Email addresses and login credentials
- Intellectual property, like trade secrets or product designs
- IT infrastructure access
- IT services, to accept financial payments
- Sensitive personal data
- US government departments and government agencies
5. Types of Cyber Attacks
1. Ransomware
Ransomware is malware designed to use encryption to force the target of the attack to pay a ransom demand. Once present on the system, the malware encrypts the user’s files and demands payment in exchange for the decryption key.

Since modern encryption algorithms are unbreakable with the technology available, the only way to recover the encrypted files is to restore the data from a backup (if available) or to pay the random demand.
2. Malware
Malware, or malicious software, is any program or file that is intentionally harmful to a computer, network or server.
Types of malware include computer viruses, worms, Trojan horses, ransomware and spyware. These malicious programs steal, encrypt and delete sensitive data; alter or hijack core computing functions and monitor end users’ computer activity.
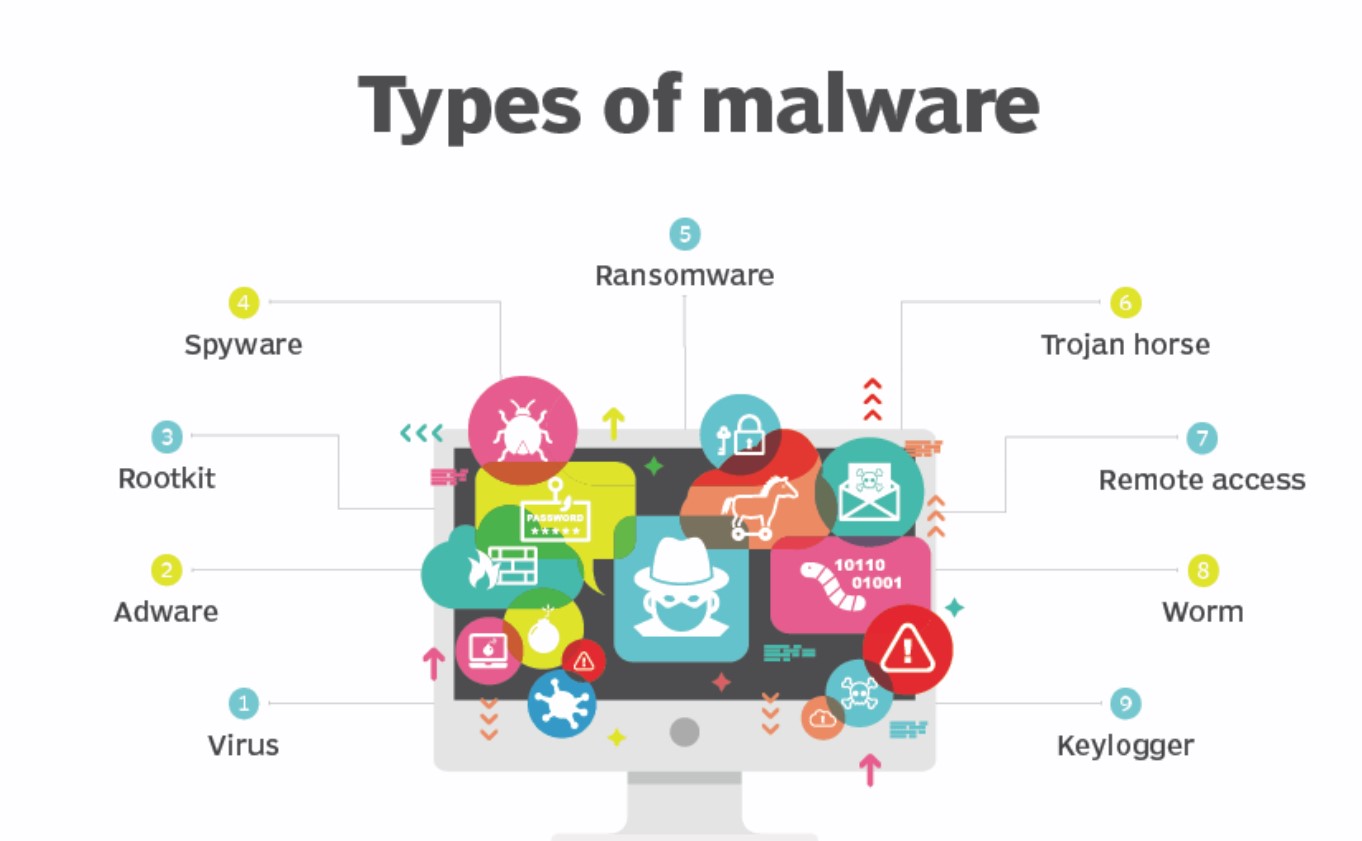
The most common forms of malware included:
- Cryptominers: Malware that uses the victim’s computer to mine cryptocurrency and make a profit for the attacker.
- Mobile Malware: Malware targeting mobile devices, including malicious applications and attacks exploiting SMS and social media apps.
- Botnet Malware: Malware that infects a system and adds it to a botnet, where it participates in cyberattacks and other illegal activity under the command of the botnet controller.
- Infostealers: Malware that collects sensitive information from an infected computer and sends it to the malware operator.
- Banking Trojans: Malware that specifically targets financial information and attempts to steal banking website credentials and similar information.
- Ransomware: Malware that encrypts the files on a user’s computer and demands payment for the decryption key.
3. Fileless Attacks
Antivirus solutions commonly attempt to detect malware on a device by inspecting each file on the device for signs of malicious content.
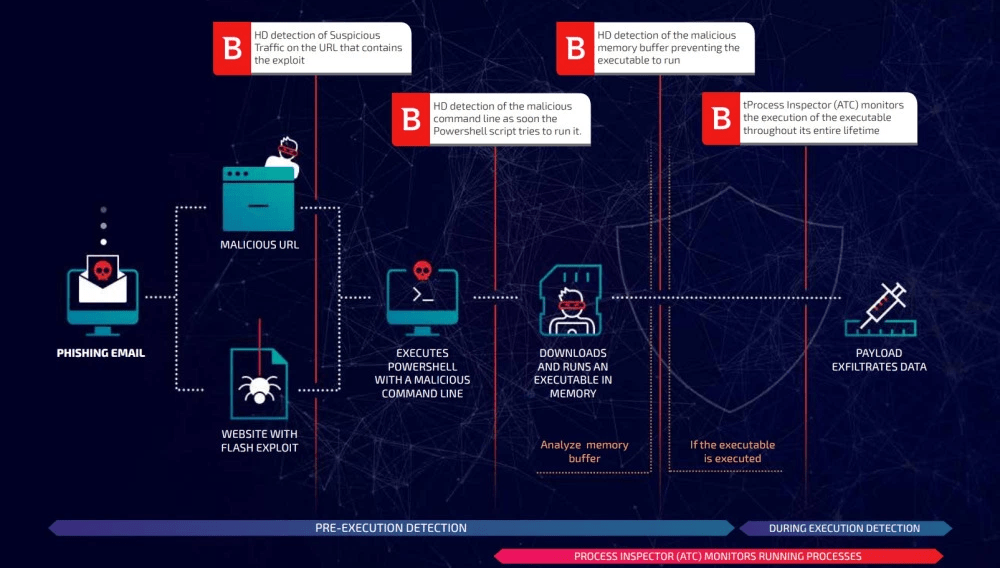
Fileless malware attempts to bypass this approach to threat detection by not using a file. Instead, the malware is implemented as a set of commands to functions that are built into the infected computer.
4. Phishing
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers.

It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
Often, it is easier to trick a user into clicking on a malicious link or opening an attachment than it is to locate and successfully exploit a vulnerability in an organization’s network.
Phishing attacks can achieve a variety of goals, including credential theft, malware delivery, financial fraud, and theft of sensitive data.
5. Man-in-the-Middle (MitM) Attack
Many network protocols are protected against eavesdroppers by encryption, which makes the traffic impossible to read.

A Man-in-the-Middle (MitM) attack bypasses these protections by breaking a connection into two pieces. By creating a separate, encrypted connection with the client and the server, an attacker can read the data sent over the connection and modify it as desired before forwarding it on to its destination.
6. Malicious Apps
Many organizations focus their cybersecurity efforts on computers, but mobile devices are a growing threat to an organization’s cybersecurity.

As employees increasingly use mobile devices to do their work and access sensitive company data, malicious mobile applications are increasingly dangerous.
These applications can do anything that desktop malware can, including stealing sensitive data, encrypting files with ransomware, and more.
7. Denial of Service Attack (DoS)
Organizations’ IT infrastructure and services – like web applications, email, etc. – are critical to their ability to do business.

Denial of Service (DoS) attacks are designed to deny access to critical services. This can be accomplished by exploiting a vulnerability in an application (causing it to crash) or by flooding a system with more data or requests than it is able to manage (rendering it unable to handle legitimate requests).
8. Zero-Day Exploit
Software contains weaknesses and vulnerabilities, and many of these vulnerabilities reach production, where they are potentially exploitable by attackers. These production vulnerabilities are discovered internally at the company, by external security researchers, or by cyberattackers.
In the third case, the cyberattackers can exploit these “zero day” vulnerabilities in the system. Until the organization manages to patch the vulnerability – rendering it safe – all users of the system are potentially vulnerable to attack.
Leave a Reply